Lock your data
The advantages of keeping digital records over paper copies are too many to enumerate. However, the lack of education and discipline when it comes to the safe handling of these records in the production industry is disturbing.
Historically, production companies have had two options for paper records: non-essential documents get shredded while the rest is filed in binders, then locked away in a dark corner. I still remember the first time I visited a storage warehouse and discovered what decades of production binders look like. From the overall seediness of the neighborhood to the flimsiness of the padlock on the door, one thing was evident enough: this was not a secure filing solution.
There exist companies that provide secure shredding and document storage. The most famous one is probably Iron Mountain, whom I discovered won’t even speak to you on the phone if you aren’t listed as an authorized contact. Although it may seem excessive, this is the level of security that we should aim for.
Today, digital records have taken over in most areas of our lives…except in our industry. Filling out a paper start form, a timecard, or receiving a paper check is still far too common. In this article, I want to explore the reason behind our outdated practices and the options we have to change this status quo.
The Stakes
“Identity theft is not a joke, Jim”. Dwight Shrute, The Office, season 4 episode 21.
This hilarious moment of television hides the horrifying reality of identity theft. Although this type of fraud seems to be on the decline (there are disagreements on the methods used to track these metrics), it’s worth remembering what identity theft is for millions of individuals:
- Losing thousands of dollars and having to fight to get the funds back
- Spending on average 330 hours to resolve the problem
- Having your name associated with various crimes, including prison records
In addition, identity theft is a scarring event. I’ve personally dealt with many freelancers who either heavily questioned or refused various onboarding methods, fearing that their identity could be stolen again. Because these victims are few, their concerns are often dismissed, and the options they are offered tend to be very limited.
Although it’s not the only reason, the identity theft risk should be enough for all of us to care more about the state of paper and digital records in our industry.
Computer literacy
The main advantage of paper is its physicality and our familiarity with the medium. Most people know how to store documents without having to be taught. It is self-evident that two locks on a door are better than one, or that a more expensive lock tends to be safer (although the Lockpicking lawyer proved this to be wrong multiple times).
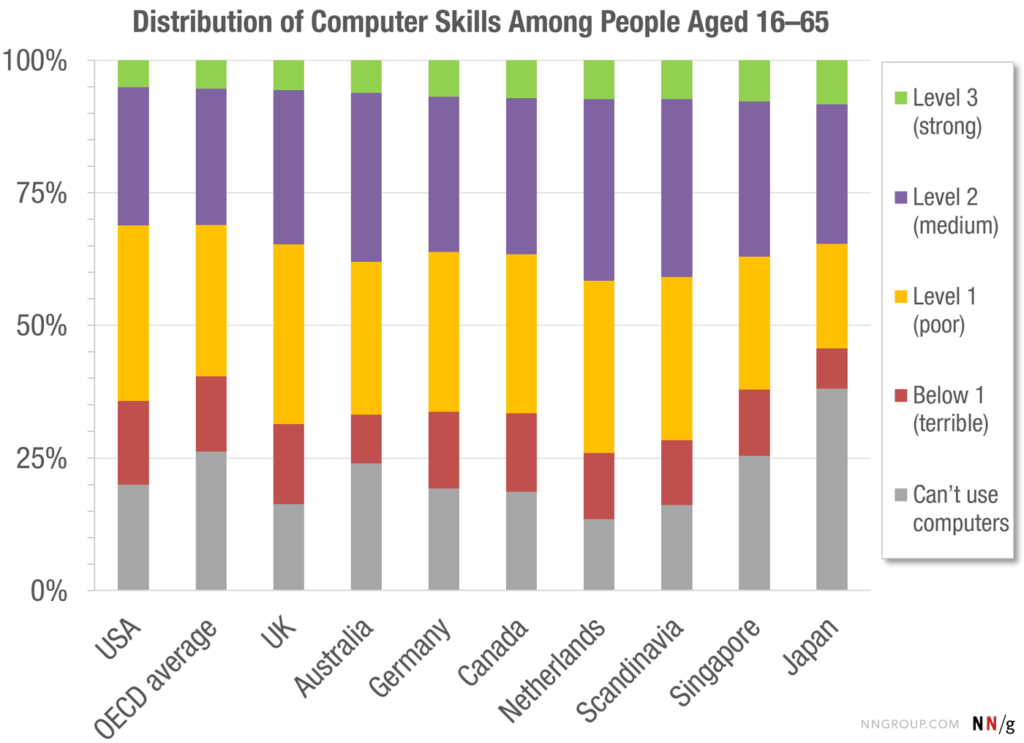
This is not the case when it comes to digital records. A 2016 study by the Nielsen group found that only 5% of the population has high computer-related abilities, and only a third of people can complete medium-complexity tasks.
The participants in this study are sorted into four levels of proficiency:
- Below 1 (a nice way to say zero) example task: “Delete this email message”
- Level 1 example task: “Find all emails from John Smith”
- Level 2 example task: “Find a sustainability-related document that was sent to you by John Smith in October last year.”
- Level 3 example task: “Calculate the percentage of the emails sent by John Smith last month were about sustainability.”
You (the reader), are most likely part of the level 3 group. However, the remaining 95% of the population isn’t. This reality, as shocking as it may be, must be taken into account when dealing with digital records in a production office.
A complex industry
One of the reasons our industry lacks behind in the digital record space is directly linked to the complexity of onboarding processes. A “regular” employee can be hired with minimal paperwork and using the same set of documents 90% of the time. The workforce in the entertainment industry can be qualified as contractors, employees, loaned out employees, and minors.
In addition, the onboarding may be the easiest part of the process. Generating accurate time cards that account for union regulations across all 50 states is near impossible. Mainstream payroll companies like ADP aren’t interested in entertainment payroll for this very reason: the complexity isn’t worth it.
Finally, the tasks I’m describing must often be done on set, requiring a great mobile user experience, a field that has only emerged in recent years. Designing a system that covers all situations in an elegant way is a challenge that hasn’t been solved to date. As a result, we are left with paper documents and human reviewers.
People
As I mentioned earlier, you can hire the services of a company that deals exclusively with the handing of paper and digital records. Their expertise will cover 90% of the issues that need to be addressed. However, this is not a satisfying solution because:
- It doesn’t apply to most smaller production companies
- It doesn’t solve for the weakest point in the chain: people.
Back in 2018, I met a security consultant with an unusual sales method. After obtaining a meeting with the head of IT for a company and pitching in their office, he would be escorted back to the building’s reception. There, he would turn back, mention to the receptionist how he had just left his coat inside and ask to get back in for just a few seconds in order to retrieve it. Once inside, he would find an employee’s vacant terminal and send an email to the head of IT.
Regardless of the technique used to obtain or exploit information, the vulnerability almost always lies with the people having access to it. Before considering any system change, the first step towards adequate information security should be to educate your team on the subject.
Dos and Donts
Passwords
Until we agree on a better alternative to them and given that everyone on your team will need a one to access any information in the production office, it’s important to maximize passwords’ usage.
The first rule of passwords: you do not talk about your password.
As I am writing this article, I find myself hesitant to share tips on creating a strong password, as it would reveal my preferences for specific methods. I encourage you to do your own research in order to share best practices with your team in person (and not in a publicly available blog post).
Although it may seem like an obvious “do”, I guarantee you that most people who work with you aren’t using a password that would qualify as “secure enough” to safeguard one person, let alone an entire roster of freelancer’s personal information.
Social Security numbers
In the production industry, we seem to love writing Social Security numbers on absolutely every document and for no reason. The first thing to acknowledge is that the moment you include a full social security number in a database, you increase your liability by multiple folds. Unless your are a payroll company, I would strongly advise against collecting anywhere that it isn’t absolutely necessary.
Here is what should appear on the various documents of the start packet:
- Deal memo: Social Security number not needed
- Start-form: Last 4 digits only (talk to your payroll provider first)
- I9: Full Social Security number
- W4: Full Social Security number
- TimeCard: Last 4 digits only
- Box rental form: talk to your payroll provider about removing any mention of a SSN.
Encryption
There is a shroud of mystery surrounding encryption. However, at its very basic level, encryption is no different than the ciphers we all decrypted as kids by swapping numbers for letters. A modern encrypted file can technically be deciphered but requires an extraordinary amount of computer resources and time.
If you would like to learn more about cryptography, I can’t recommend enough this mini-series by Art of the Problem.
In any instance where you need to collect a full social security number, you should do so via a service that offers encryption. Most form signature tools offer this service, but as a rule, it’s worth looking into a company’s stance on information security before offering your own personal information or asking others to provide the same.
The main certificate of compliance for information security is called SOC 2. Companies that are certified have undergone an audit to verify that they provide their clients with features like encryption and two-factor authentication, and run their operations using various access controls and intrusion detection protocols.
Access
We mentioned passwords above, but we haven’t addressed the subject of access yet. When we talk about information security, it is important to understand the concepts of “confidentiality” and “availability”.
As a production office grows, it becomes increasingly more difficult to keep a strong ethic when it comes to information access. As a rule of thumb, information should not be made available to anyone unless they truly need it since the risk of a breach increases with every new authorized user through negligence or theft.
Any respectable production office’s fist step towards information control should be to implement the use of a password manager. Setting up this kind of software will allow you to streamline the granting and revoking of access to full-time employees and freelancers but make sure to first establish the process that dictates who can be privileged to each database you keep.
Take security seriously
Regardless of the medium used to store information, information security should be on your to-do list. The video production industry is behind the times when it comes to the proper storage of personal confidential data and faces difficulties that are unique to the industry. The constant use of temporary labor creates tough challenges on both sides of the information handshake.
The consequences of ignoring proper information security protocols range from annoying (having to work with an individual who refuses digital paperwork) to dramatic as compromised data and identity theft can cost both production companies and individuals significant amounts of time and money.
As with any operational process, information security can be implemented step by step using logic reasoning and adequate tools.

0 Comments